Keeping assets and resources secure is a top priority for all IT and security teams as more businesses migrate their resources and assets into the cloud. An industry worth billions of dollars is cybercrime. Because of data loss and reputational damage, failing to secure your business may be expensive.
In order to reduce and mitigate risks across your whole estate and enhance the overall cloud security posture, Microsoft Azure offers a variety of threat protection and detection solutions.
In this article, we’ll study Microsoft Defender for Cloud’s capabilities, including secure score, and learn about cloud security posture management (CSPM). The upgraded security features of Microsoft Defender for Cloud will also be covered. Finally, you’ll discover more about Azure’s security baseline and benchmark.
Cloud security posture management
A relatively new class of tools called cloud security posture management (CSPM) is designed to help you manage your cloud security better. When a threat is discovered, it evaluates your systems and immediately notifies security staff in your IT department. CSPM monitors and prioritizes security features and upgrades using the tools and services available in your cloud environment.
Following are the tools and services that CSPM uses:
- Zero Trust-based access control: reflecting the active danger level when making judgments about access controls.
- Real-time risk scoring: to give insight into the main risks.
- Threat and vulnerability management (TVM): creates a comprehensive understanding of the organization’s risk and attack surface and incorporates it into engineering and operational decision-making.
- Discover risks: to comprehend how corporate intellectual property is exposed to data on authorized and unauthorized cloud services.
- Technical policy: Apply safeguards to the technological systems you inspect and enforce the organization’s standards and rules.
- Threat modeling systems and architectures: combined with other particular uses.
The main objective of a cloud security team engaged in posture management is to regularly report on and enhance the organization’s security posture by emphasizing limiting a possible attacker’s return on investment (ROI).
Microsoft Defender for Cloud
Microsoft Defender for Cloud is an tool for managing security posture and preventing threats. Defender for Cloud improves the security posture of your cloud resources and safeguards workloads operating on Azure, hybrid, and other cloud platforms with its integrated Microsoft Defender plans.
As you manage the security of your resources and workloads both on-premises and in the cloud, Microsoft Defender for Cloud satisfies 3 main needs:
- Continuously assess – Understand your security posture and keep an eye out for weaknesses.
- Secure – Harden all services and resources that are linked.
- Defend – Threats to resources, workloads, and services can be found and removed.
Cloud workload protection and cloud security posture management are the two main pillars of cloud security that are covered by the capabilities of Microsoft Defender for Cloud that meet these standards.
Cloud security posture management (CSPM)
The posture management tools in Microsoft Defender for Cloud offer the following.
- Visibility – to better understand the security position you are now in.
- Hardening guidance – to effectively and efficiently assist you in enhancing your security.
Visibility and hardening recommendations
You may accomplish these objectives thanks to Microsoft Defender for Cloud’s secure score function, which is its main component. Your resources, subscriptions, and organization are continuously analyzed for security flaws by Microsoft Defender for Cloud. The results are then combined into one score, which allows you to quickly determine your present security position. The higher the score, the lower the determined danger level.
In addition, Microsoft Defender for Cloud offers advice for hardening systems based on any discovered security flaws and weaknesses. Security controls are collections of recommendations. Each control represents your exposed attack surfaces and is a logical set of connected security suggestions. Only after you implement all of the suggestions for a particular resource under a control do you see a rise in your score. Use these security guidelines to improve the Azure, hybrid, and multi-cloud resources’ security posture.
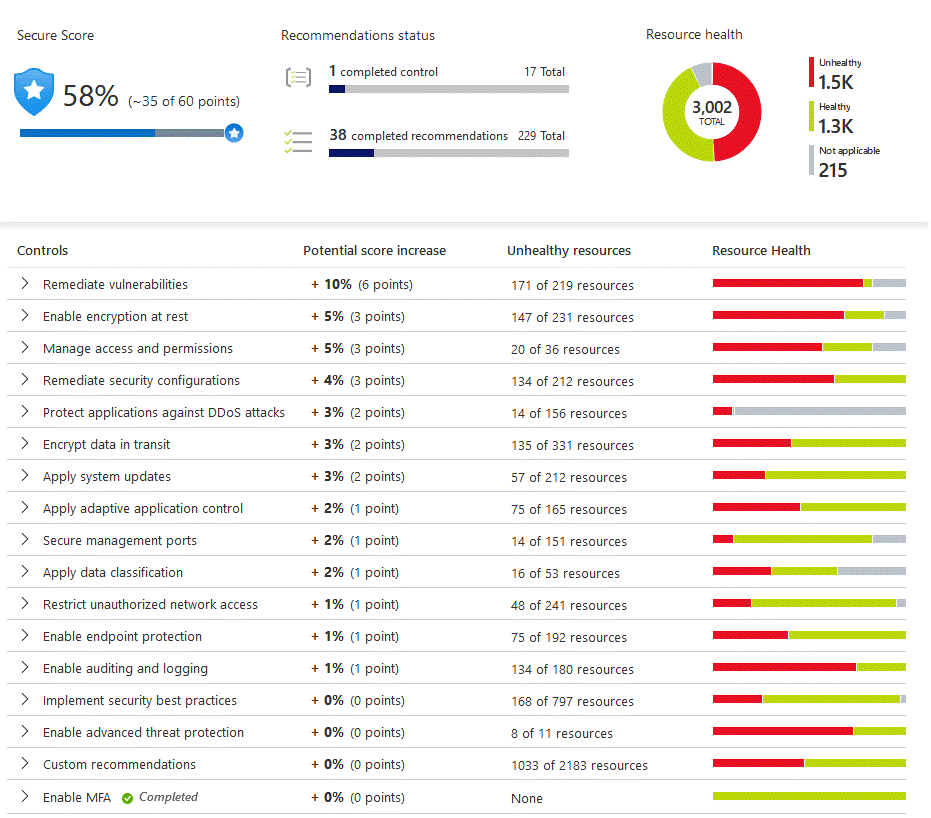
You can know about how to use the secure score and the hardening suggestions in Microsoft Defender for Cloud are shown in the interactive click-through that follows. To begin, click here and then adhere to the on-screen instructions.
Cloud workload protection (CWP)
Workload protection in the cloud is the second pillar of security. Microsoft Defender for Cloud can identify and eliminate threats to resources, workloads, and services thanks to its capabilities for protecting cloud workloads. Protections for your workloads in the cloud are provided by integrated Microsoft Defender plans that are tailored to the categories of resources in your subscriptions and offer better security features.
Enhanced security of Microsoft Defender for Cloud
There are two modes available for Microsoft Defender for Cloud:
- Microsoft Defender for Cloud (Free) – On all of your Azure subscriptions, Microsoft Defender for Cloud is activated for no additional charge. You can secure your Azure resources by using this free mode, which offers the secure score and its associated features, including security policy, continuous security assessment, and actionable security advice.
- Microsoft Defender for Cloud with enhanced security features – A single security management and threat prevention across your workloads is provided by enabling enhanced security, which extends the capabilities of the free mode to workloads operating in Azure, hybrid, and other cloud platforms. Protections for your workloads in the cloud are provided by integrated Microsoft Defender plans that are customized to the categories of resources in your subscriptions and offer better security features.
Let’s know more about Microsoft Security Solutions in the next article.










