In this article let’s learn about some of the security tools which help you in keeping your infrastructure and data safe when working in the cloud. There are lots of factors to consider when it comes to protecting your applications and data. Let’s look at how Azure can help you protect workloads that you run in the cloud and on-premises.
This article will mainly instruct you these things.
- Using Azure Security Center, you can improve your overall security and protect against threats.
- Using Azure Sentinel, you can collect and act on security data from a variety of sources.
- In Azure Key Vault, you can securely store and access sensitive information like passwords and encryption keys.
- Using Azure Dedicated Host, you can manage dedicated physical servers to host your Azure VMs for Windows and Linux.
Azure Security Center
Azure Security Center is a monitoring service that provides visibility into your security posture across all of your Azure and on-premises services. Security posture refers to your cybersecurity policies and controls, as well as your ability to predict, prevent, and respond to security threats.
This can help you with,
- Examine security settings on-premises and in the cloud.
- Apply necessary security settings to new resources as they come online.
- Make security recommendations based on your existing configurations, resources, and networks.
- Continuously monitor your resources and run automated security assessments to detect potential vulnerabilities before they are exploited.
- Use machine learning to detect and prevent the installation of malware on your virtual machines (VMs) and other resources. You can also use adaptive application controls to define rules that list allowed applications, ensuring that only the applications you allow are allowed to run.
- Detect and analyze potential inbound attacks, as well as investigate threats and any post-breach activity.
- Provide network ports with just-in-time access control. This reduces your attack surface by ensuring that the network only allows the traffic you require at the time you require it.
This brief video explains how Security Center can help you in strengthening your networks, securing and monitoring your cloud resources, and improving your overall security posture.
The company can use Security Center to make a detailed analysis of various components in its environment, and an example of what you might see in Azure Security Center is shown below.
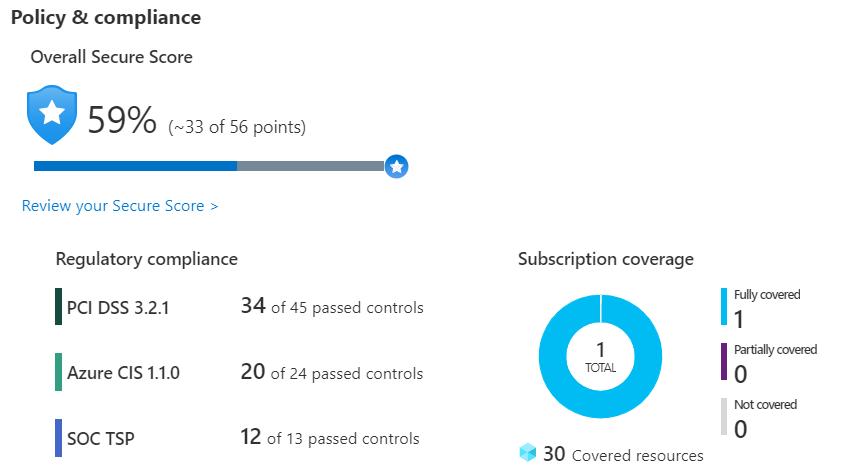
If the company is required to conform to the Payment Card Industry’s Data Security Standard (PCI DSS). This report demonstrates that the company has the resources necessary to remediate.
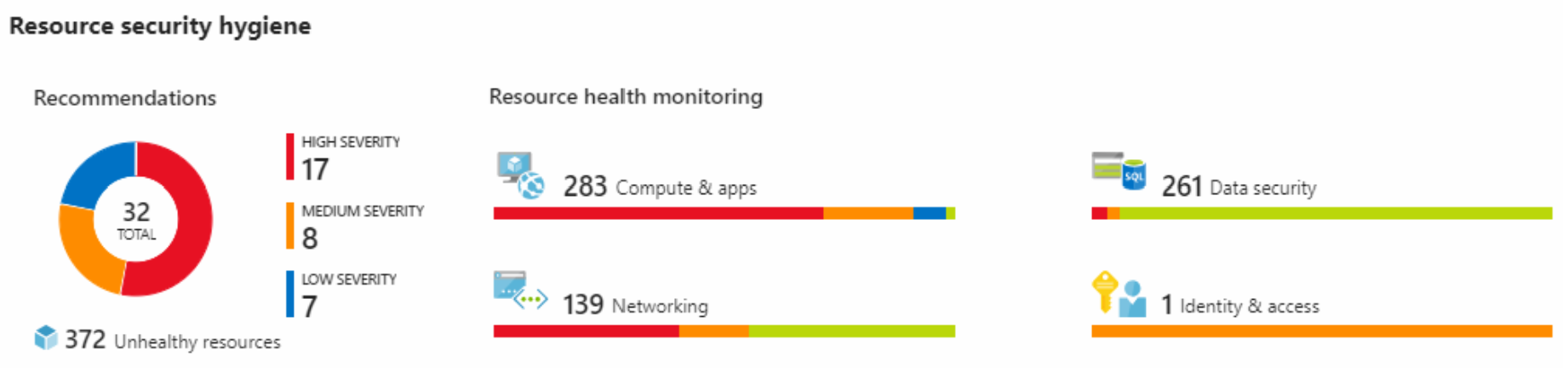
Company can see the security health of its resources in the Resource security hygiene section. Recommendations are categorized as low, medium, or high to help prioritize remediation actions. Here’s an example.
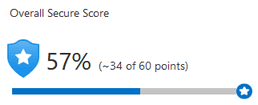
Secure Score
The secure score is a metric that evaluates an organization’s overall security.
The secure value is computed by security controls, which are groups of related security recommendations. Your score is calculated as the ratio of security controls that you meet. The higher your score, the more security controls you satisfy. When you complete all of the recommendations for a single resource within a control, your score rises.
Here’s an example from the Azure portal of a 57 percent, or 34 out of 60 point score.
Secure score can help you:
Provide an update on your organization’s security posture.
Enhance your security posture by providing availability, visibility, guidance, and control.
Establish key performance indicators and compare them to benchmarks (KPIs).
Protect against threats
Advanced cloud defense capabilities for VMs, network security, and file integrity are all included in Security Center.
- Just-in-time VM access – The company can set up just-in-time access to VMs. This access restricts traffic to specific network ports of VMs by default, but allows it for a limited time if an administrator requests and approves it.
- Adaptive application controls – The company has control over which applications are allowed to run on its virtual machines. In the background, Security Center examines the processes running on a VM using machine learning. This process generates alerts informing the company about unauthorized applications running on its virtual machines.
- Adaptive network hardening – The Security Center can monitor the VMs’ internet traffic patterns and compare them to the company’s current network security group (NSG) settings. The Security Center can then make recommendations about whether the NSGs should be further restricted and provide remediation steps.
- File integrity monitoring – Changes to important files on both Windows and Linux, registry settings, applications, and other aspects that may indicate a security attack can also be monitored by the company.
Respond to security alerts
Security Center can be used to receive a centralized view of all security alerts. The company can then dismiss false alerts, investigate them further, manually remediate alerts, or use an automated response with workflow automation.
Workflow automation is accomplished through the use of Azure Logic Apps and Security Center connectors. A threat detection alert or a Security Center recommendation can trigger the logic app, which can be filtered by name or severity. The logic app can then be configured to perform an action, such as sending an email or posting a message to a Microsoft Teams channel.
Detect and respond to security threats
A dedicated security information and event management (SIEM) system can help with large-scale security management. A SIEM system collects security data from a variety of sources (as long as those sources support an open-standard logging format). It also includes threat detection and response capabilities.
Azure Sentinel is Microsoft’s SIEM system in the cloud. It employs intelligent security analytics as well as threat analysis.
Azure Sentinel
You can use Azure Sentinel to:
- Collect large amounts of cloud data from all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
- Detect previously unknown threats Reduce false positives by leveraging Microsoft’s extensive analytics and threat intelligence.
- Artificial intelligence can be used to investigate threats. Examine suspicious activities at scale, drawing on Microsoft’s years of cybersecurity experience.
- Respond quickly to incidents Use the built-in orchestration and automation features for common tasks.
Azure Key Vault
This is an another service you can use.Azure Key Vault is a centralized cloud service for centrally storing an application’s secrets. It ensures secure access to sensitive information by enabling access control and logging.
Azure Key Vault can help you in the following ways:
- Keep secrets safe. Key Vault can be used to securely store and restrict access to tokens, passwords, certificates, API keys, and other secrets.
- Control encryption keys Key Vault can be used as a key management solution. Key Vault simplifies the creation and management of encryption keys used to encrypt your data.
- Control SSL/TLS certificates Key Vault lets you provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for both Azure and internal resources.
- Keep secrets safe with hardware security modules (HSMs) These secrets and keys can be safeguarded using software or FIPS 140-2 Level 2 validated HSMs.
Benefits of Azure Key Vault
- Centralized application secrets – Centralizing the storage of your application secrets allows you to control their distribution and reduces the likelihood of accidental leakage.
- Securely stored secrets and keys – Azure employs industry-standard algorithms, key lengths, and hardware security modules (HSMs). Key Vault access requires proper authentication and authorization.
- Access monitoring and access control – Access to your application secrets can be monitored and controlled.
- Simplified administration of application secrets – Key Vault simplifies the enrollment and renewal of certificates issued by public certificate authorities (CAs). You can also use standard certificate management tools to scale up and replicate content within regions.
- Integration with other Azure services – Key Vault can be integrated with storage accounts, container registries, event hubs, and many other Azure services. The secrets stored in Key Vault can then be securely referenced by these services.










