When building a solution, we should consider the various layers of security that Cognitive Services offers. In this article we will learn how to manage network security and consider authentication for cognitive services.
Consider authentication
Accessibility to the resources of cognitive services is often controlled by subscription keys. The control of who has access to these keys is important for security.
To protect against the possibility of keys being shared with or accessed by unauthorized individuals, you should regularly regenerate keys. Both the visual interface in the Azure portal and the az cognitiveservices account keys regenerate Azure command-line interface (CLI) command can be used to regenerate keys.
Two keys are given for each cognitive service, allowing you to regenerate keys without affecting service. To achieve the following:
- Configure all production applications to use key 2.
- Regenerate key 1
- Switch all production applications to use the newly regenerated key 1.
- Regenerate key 2
Protection of keys with Azure Key Vault
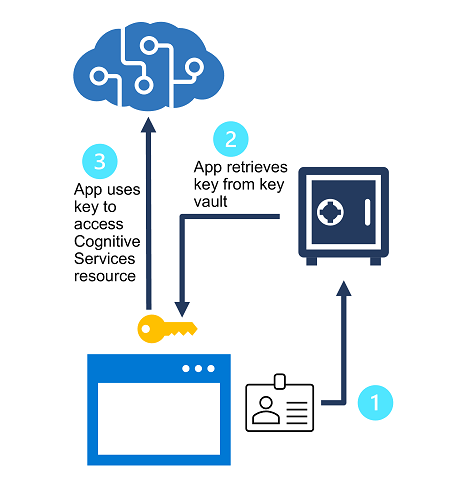
You can safely store secrets (such as passwords and keys) in the Azure service known as Azure Key Vault. Security principals, which you can think of as user identities that are authenticated using Azure Active Directory, are given access to the key vault (Azure AD). To create a managed identity for the application, administrators can assign a security principal to it (in which case it is called to as a service principal). The program can then access the key vault with this identity and get a secret that it has access to. The chance of the secret being compromised by being hard-coded in an application or saved in a configuration file is reduced by limiting access to it in this way.
The Azure Key Vault can be used to hold the subscription keys for a cognitive services resource, and client apps that use the service can be given a controlled identity. The key can be retrieved as needed from the key vault by the apps without running the risk of disclosing it to unauthorized users.
Token-based authentication
Some Cognitive Services enable (or even demand) token-based authentication when using the REST interface. In these situations, the subscription key is provided in the initial request for an authentication token that has a 10-minute expiration date. The token must be provided in order for subsequent requests to verify that the caller has been authenticated.
Azure Active Directory authentication
For apps and services running in Azure, you can also provide access to particular service principals or managed identities by using some cognitive services that enable Azure Active Directory authentication. Read more about authentication options for Cognitive Services from here.
Network security
To make sure that unauthorized users cannot access the services you are protecting, network security is an essential measure. It’s usually a good idea to restrict what people can view because they can’t compromise on what they can’t see.
Network access restrictions
All networks can access Cognitive Services by default. Some individual Cognitive Services services, like Text Analytics, Face, Computer Vision, and others, can be set up to limit access to particular network addresses, including addresses on virtual networks as well as addresses on the public Internet.
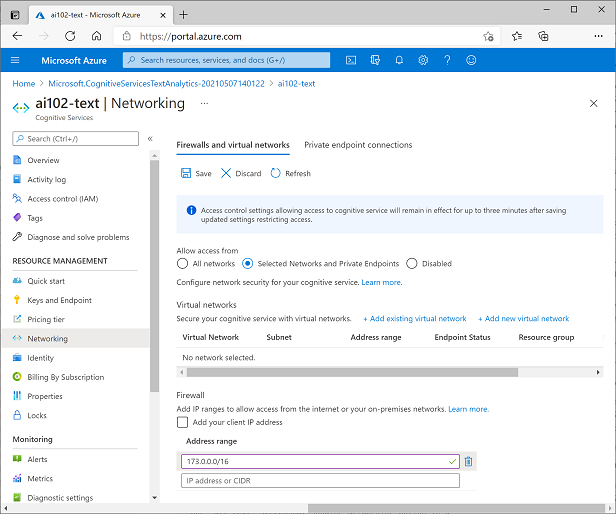
When network limitations are active, a client trying to connect from a prohibited IP address will see an Access Denied error.










