Authentication technologies are used to restrict who has access to a system. When a process or user attempts to access a system, the authentication scheme determines whether the requesting process or user is recognized by the system. When a user or process is granted access, they are referred to as authenticated. Authentication protects a system from unauthorized access by granting access only to authenticated users or processes.
By restricting access to specific resources, authorization mechanisms provide a more granular level of access control. When an authenticated process or user attempts to access a specific resource, the authorization scheme checks to see if the user or process has been granted permission to do so. Authorization also takes into account the type of access requested, such as read-only, write-only, or administrative.
Authentication and authorization work together to help you manage your corporate identities and ensure your organization’s security. You can use these technologies to:
- Control access to your company’s and its resources.
- Securely store corporate passwords and secrets.
- Integrate your user and application identity solution with Azure AD.
Identity and access management (IAM) Design
Azure Architects create identity and access management (IAM) solutions to implement authentication and authorization. These solutions must be compatible with all users, applications, and devices. A strong identity and access management solution should provide unified identity management, secure adaptive access, simplified identity governance, and a unified user experience.

Consider the following characteristics of a strong IAM solution as you consider your authentication and authorization options
- Unified identity management: To improve visibility and control, manage all of your identities and access to all of your applications in one place, whether they’re in the cloud or on-premises.
- Seamless user experience: Provide a simple, quick sign-in experience to keep your users productive, cut down on time spent managing passwords, and boost end-user productivity.
- Secure adaptive access: Protect user access to resources and data by implementing strong authentication and risk-based adaptive access policies that do not jeopardize the user experience.
- Simplified identity governance: Control all users’ and administrators’ access to applications and data. Only authorized users have access thanks to automated identity governance.
Considerations for Using IAM
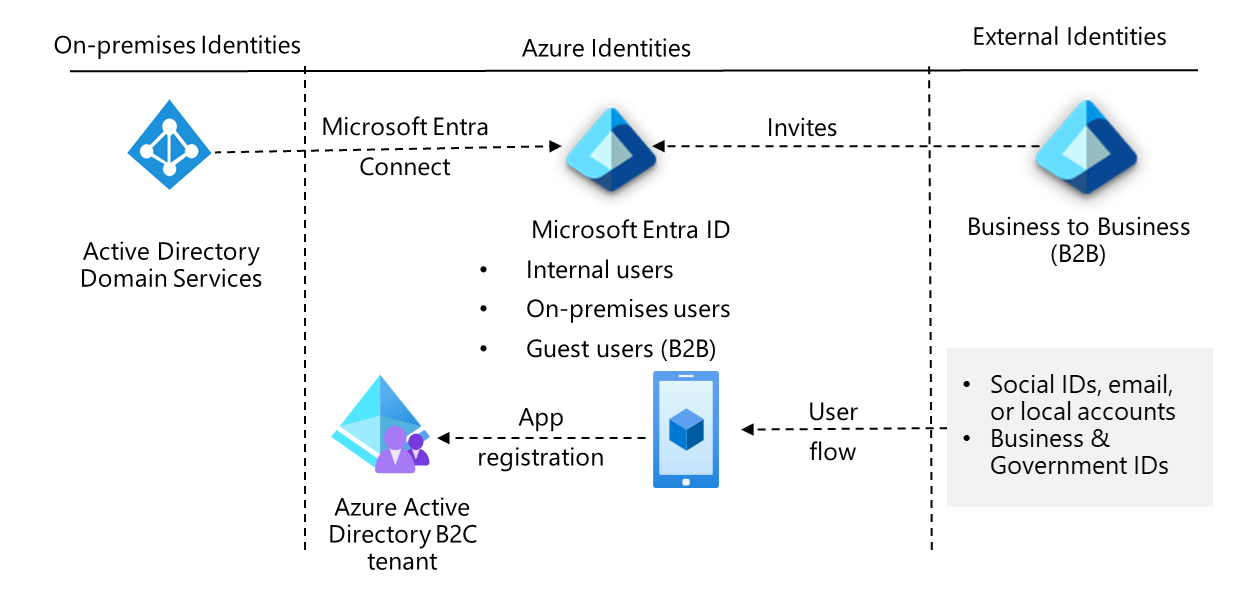
Azure Active Directory: Create a solution with Azure AD that combines core directory services, application access management, and identity protection. Azure AD is a cloud-based or hybrid identity and access management system that can be used by employees.
Business-to-Business (B2B) requirements: Support collaboration for company guests and external business partners such as suppliers and vendors. To support business-to-business operations, build your solution with Azure AD B2B (business-to-business).
Business-to-Customer scenarios: Control how customers use company apps to sign up, sign in, and manage their profiles. Create an Azure AD B2C (business-to-customer) solution to support customer-focused operations.
Azure Active Directory Design
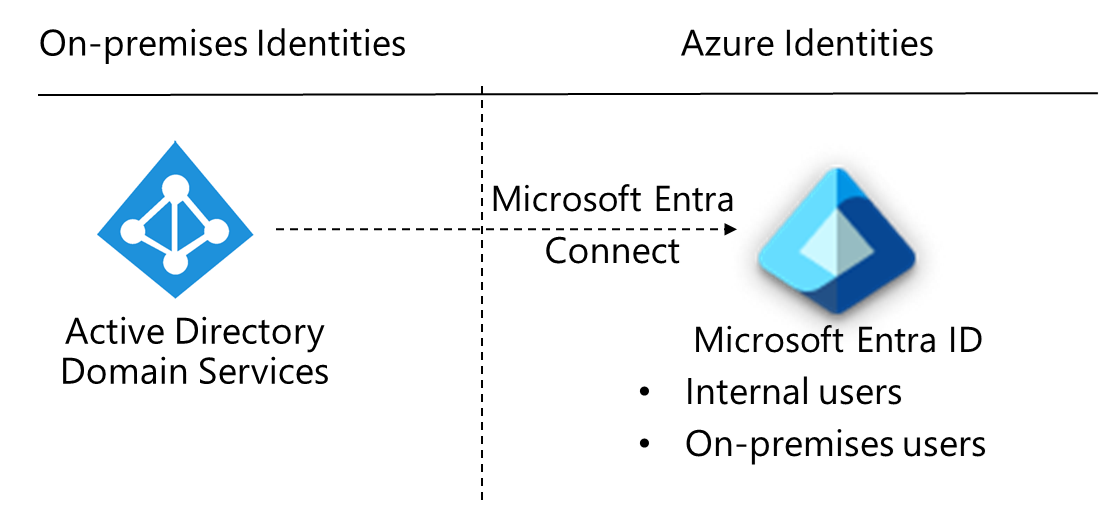
Azure AD is the Azure identity and access management solution. Azure AD is a cloud-based directory and identity management service that supports multiple tenants. It is a single solution that combines core directory services, application access management, and identity protection. Azure Active Directory can be used in cloud or hybrid environments.
Important things about Azure AD identity management
- You can use Azure AD as a cloud-only identity provider for all of your employee user accounts.
- The cloud-only identity solution manages and protects your accounts’ identities, including role-based access control (RBAC), conditional access, and access reviews.
- Azure AD also provides a hybrid identity solution for managing identities in hybrid environments.
- You can import on-premises identities into Azure AD using Azure AD Connect or Azure AD Connect cloud sync. After the on-premises accounts are moved to Azure AD, they will benefit from easier management and identity protection.
Azure Active Directory business-to-business (B2B) Design
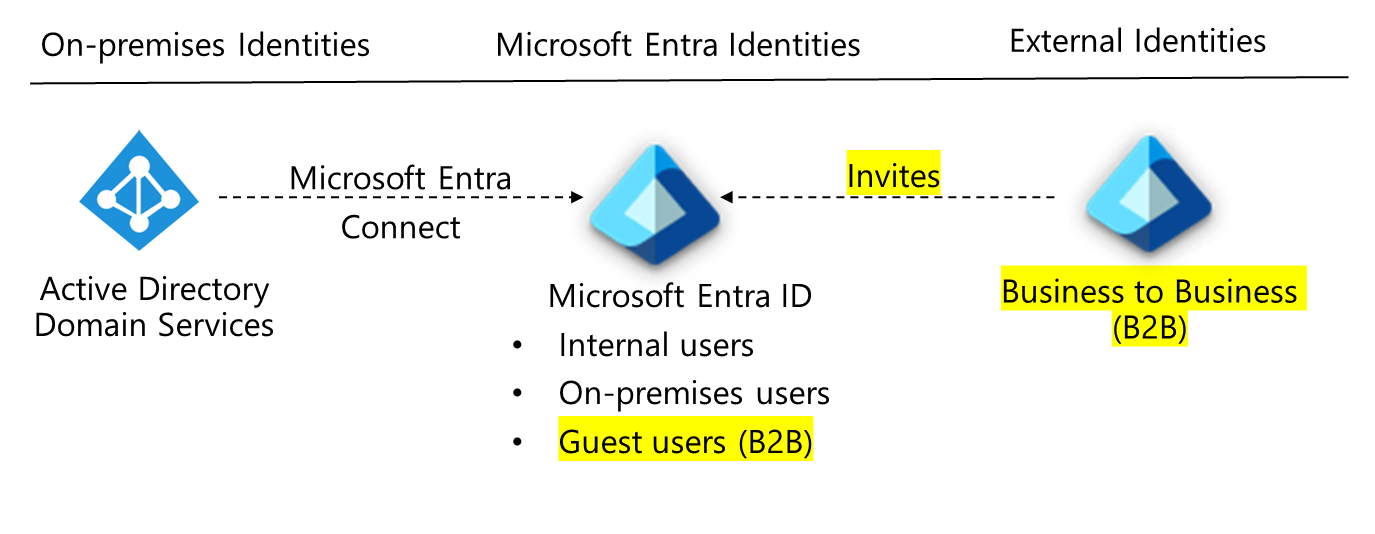
Every organization must collaborate with outside users. Business-to-business (B2B) collaboration with Azure AD is a feature that allows you to securely collaborate with external partners. Your partner users have been invited as guests. You retain control over what they have access to and how long they have it.
Azure AD B2B Facts
The external partner uses their own identity management solution with Azure AD B2B. Azure Active Directory is not required.
The company is not required to manage external accounts or passwords.
External users collaborate with the organization by using their identities. The identities are managed either by the partner or by an external identity provider on their behalf.
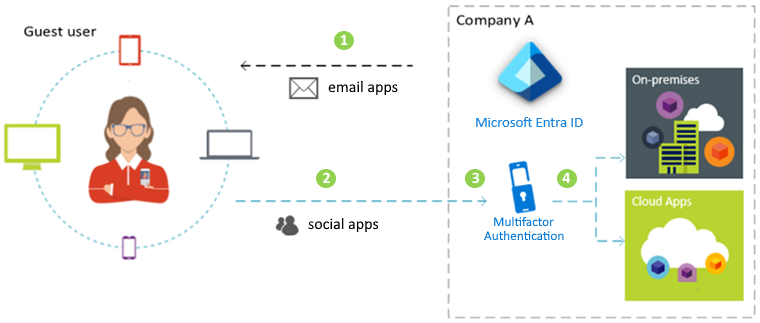
Azure Active Directory B2C (business-to-customer) Design
Azure AD B2C is a type of Azure AD tenant used to manage customer identities and app access. Azure AD B2C requires an Azure AD tenant, but this tenant is not the same as your organization’s Azure AD tenant.