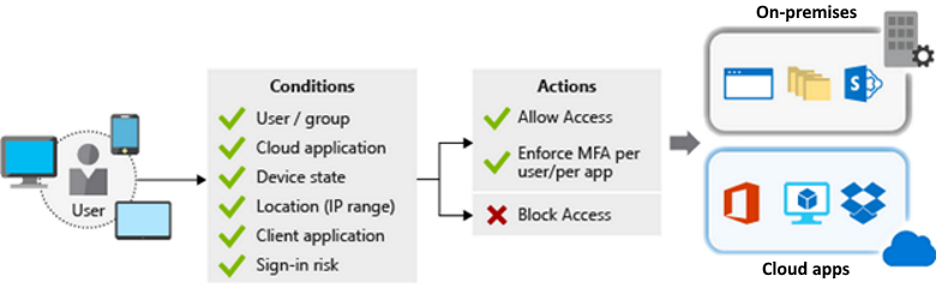
From last article we discussed about authentication and authorization solutions. Before we continue learning let’s refresh our memory. Click here to read the previous articles.Azure Active Directory uses Conditional Access to grant (or deny) access to resources. Conditional Access examines who the user is, where the user is, and from what device the user is requesting access when a user signs in. Conditional Access can grant access, enforce multifactor authentication (MFA), or deny access based on these signals.
Conditional Access Facts
- Granular control is supported by MFA. You can use MFA selectively and only require it for specific users.
- Named locations can be used in conjunction with app policies to control access in Azure AD.
- Only approved client apps can gain access to services.
- App access can be restricted to managed devices that meet your security and compliance requirements.
- Untrusted sources, such as those from an unknown or unexpected location, can be blocked.
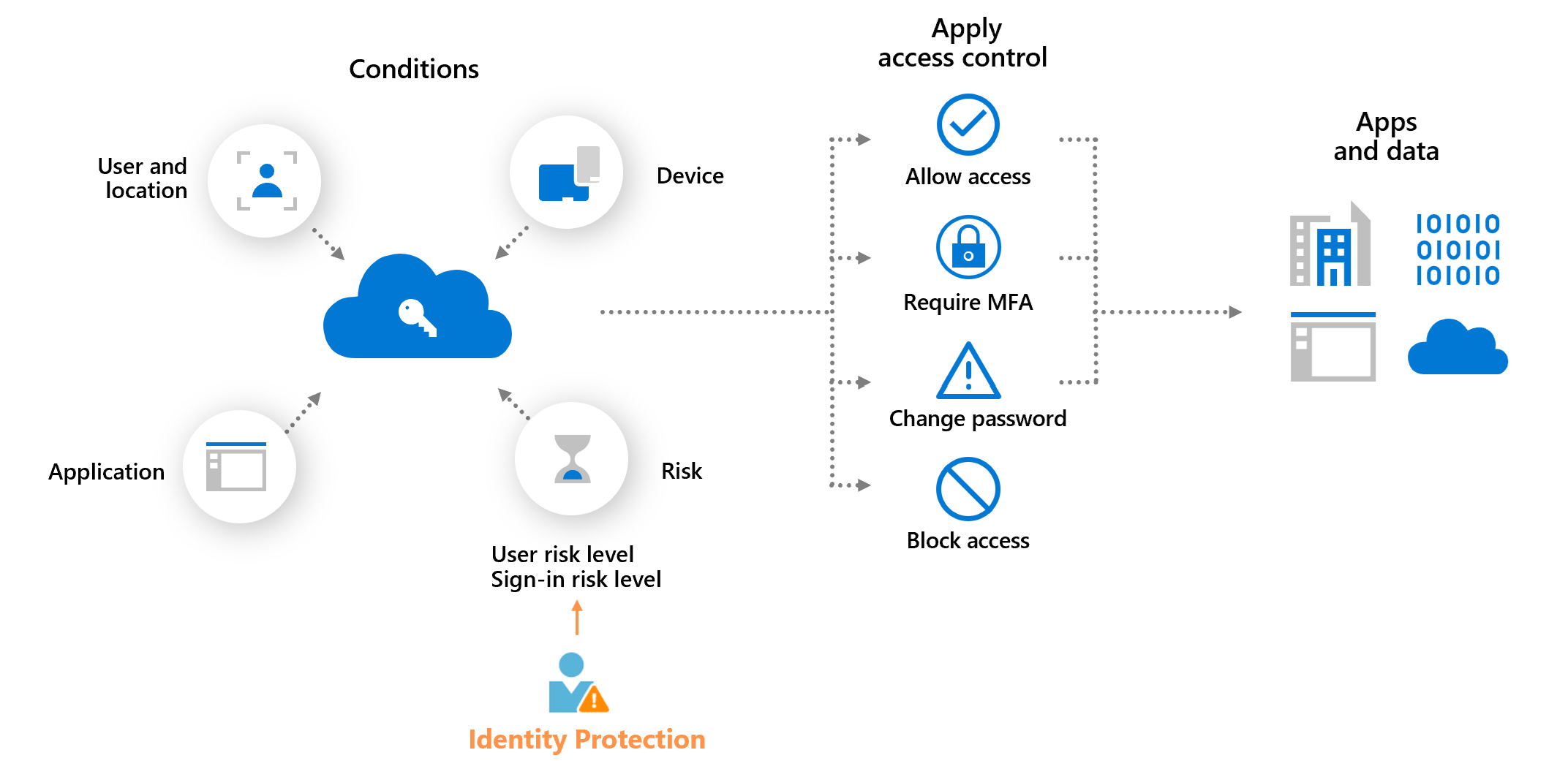
Design for identity protection
Identity Protection is a tool that enables organizations to complete three critical tasks.
- Detect and remediate identity-based risks automatically.
- Investigate risks with data from the Azure portal.
- Data from risk detection can be exported to other tools.
The signals generated by Identity Protection and fed into it can be exported to other tools. You learned how the Conditional Access tool can make decisions based on the policies of your organization. You can send this information to a security information and event management (SIEM) tool for further investigation by using Identity Protection.
Identity Protection Facts
- Identity Protection detects risk policies, which include any suspicious actions associated with user accounts in the directory.
- Two risk policies are being evaluated: user risk and sign-in risk.
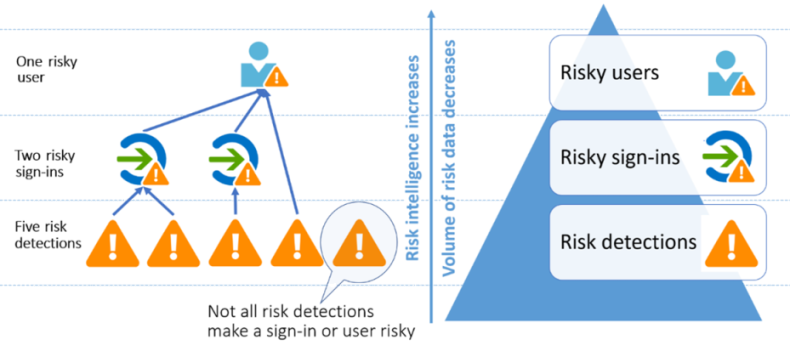
The probability that a given identity or account will be compromised is represented by user risk. A valid user’s credentials are leaked as an example. Offline, Microsoft’s internal and external threat intelligence sources are used to calculate user risks. Leaked credentials and Azure AD threat intelligence are two examples of user risks.
Sign-in risk is the probability that a given sign-in (authentication request) will be denied by the identity owner. Sign-in risk can be calculated both online and offline. Anonymous IP address, Atypical travel, Malware-linked IP address and Password spray are some of examples of Sign-in risk.
Design for access reviews










