We’ll learn about Azure Active Directory in this article, including what it is and what types of identities it supports.
We can no longer rely on its network border in terms of security. Identity has become the new security boundary for allowing workers, partners, and customers to communicate safely. Our company can handle all elements of identity security by using an identity provider.
This lesson introduces you to Microsoft’s cloud-based identity and access management solution, Azure Active Directory (Azure AD). You’ll learn about the advantages of using a cloud-based identity provider, such as single sign-on for users, in this topic. You’ll also learn about the various Azure AD versions, the identity types that Azure AD supports, and how to utilize it to support external users.
what is Azure Active Directory
Microsoft’s cloud-based identity and access management service, Azure Active Directory (Azure AD), is a cloud-based identity and access management service. Organizations utilize Azure AD to allow their workers, visitors, and others to sign in and access resources such as:
- Internal resources, such as apps on your company’s intranet and internal network, as well as cloud apps created by your own team.
- External services utilized by your company, such as Microsoft Office 365, the Azure portal, and any SaaS apps.
By delivering a single identity system for cloud and on-premises apps, Azure AD streamlines the way companies manage permission and access. Azure Active Directory may be connected with your current on-premises Active Directory, with other directory services, or as a stand-alone service.
Organizations can also use Azure AD to securely enable the usage of personal devices like smartphones and tablets, as well as collaborate with business partners and customers.

IT administrators use Azure AD to manage access to corporate apps and resources depending on business needs. When accessing critical corporate resources, it may also be set up to demand multi-factor authentication. Azure Active Directory (Azure AD) can be used to automate user provisioning between a Windows Server AD and cloud apps, such as Microsoft 365. Finally, Azure Active Directory (Azure AD) delivers powerful tools for automatically protecting user identities and credentials, as well as meeting an organization’s access governance needs.
Azure AD is used automatically by Azure services, Microsoft 365, and Dynamics 365 subscribers. An Azure AD tenancy is automatically created for each Microsoft 365, Office 365, Azure, or Dynamics 365 Online subscription. Azure AD is a standards-based strategy that allows developers to add single sign-on (SSO) to their apps so that users can sign in using their current credentials.
Available Azure AD editions
Azure AD is available in four editions: Free, Office 365 Apps, Premium P1, and Premium P2.
- Azure Active Directory Free: You can use the free edition to manage users and groups, synchronize with on-premises Active Directory, produce basic reports, arrange self-service password change for cloud users, and enable single sign-on across Azure, Microsoft 365, and many popular SaaS apps. Subscriptions to Office 365, Azure, Dynamics 365, Intune, and Power Platform include the free edition.
- Office 365 Apps: The Office 365 Apps edition adds self-service password reset for cloud users and device write-back, which provides two-way synchronization between on-premises directories and Azure AD, to the free version. Azure Active Directory’s Office 365 Apps edition is included in Office 365 E1, E3, E5, F1, and F3 subscriptions.
- Azure Active Directory Premium P1: All of the functionality from the free and Office 365 applications editions are included in the Premium P1 edition. Advanced administration features include dynamic groups, self-service group management, Microsoft Identity Manager (an on-premises identity and access management suite), and cloud write-back capabilities, which allow on-premises users to reset their passwords themselves.
- Azure Active Directory Premium P2: P2 includes all of the Premium P1 capabilities, as well as Azure Active Directory Identity Protection, which allows you to provide risk-based Conditional Access to your apps and sensitive corporate data. P2 also includes Privileged Identity Management, which aids in the discovery, restriction, and monitoring of administrators and their access to resources, as well as providing just-in-time access as required.
Azure AD identity types
Users, service principals, managed identities, and devices are all handled via Azure Active Directory. We’ll look at each form of Azure AD identity in this article.
User
A user identity is a representation of anything that Azure Active Directory manages. In Azure AD, both employees and visitors are represented as users. You can form a group if you have several users with the same access requirements. Instead of assigning access privileges individually, you use groups to provide access permissions to all members of the group.
By using this link, you can add a new user to Azure Active.
Service principal
A service principal is a type of security identification that apps and services use to access Azure resources.
An application must first register with Azure AD in order to assign its identity and access functions to Azure AD. During the registration process, a globally unique app object is created and saved in your home tenancy or directory. In each tenancy where the application is utilized, a service principle is established that refers to the globally unique app object. The service principle specifies how the app works in the tenancy, including who can use it and what resources it has access to.
Managed identity
In Azure AD, a managed identity is handled automatically. Managed identities are commonly used to keep track of the credentials needed to connect a cloud application to an Azure service.
System-assigned and user-assigned identities are the two forms of managed identities.
System-assigned: You can enable a managed identity directly on a service instance in some Azure services. When you activate a system-assigned managed identity, an identity in Azure AD is established that is linked to the service instance’s lifetime. When you destroy a resource, Azure immediately deletes your identity. By design, this identity can only be used to request tokens from Azure AD by that Azure resource.
User-assigned: A managed identity can also be created as a stand-alone Azure resource. A user-assigned managed identity is associated with one or more Azure service instances. A user-issued managed identity can be created and assigned to one or more Azure service instances. The identity is controlled independently from the resources that use it using user-assigned managed identities.
Device
A device is a piece of hardware such as a smartphone, a laptop, a server, or a printer. In Azure AD, device IDs may be configured in a variety of ways to ascertain attributes such as who owns the device. Using solutions like Microsoft Intune to manage devices in Azure AD helps a business to secure its assets while maintaining security and compliance standards. Through these devices, Azure AD also provides single sign-on to devices, applications, and services from anywhere.
Types of external identities
External Identities in Azure Active Directory is a collection of features that enables enterprises to grant access to external users such as clients and partners. Customers, partners, and other guest users can sign in using their “own identities.”
External users can take use of this feature thanks to Azure AD’s support for external identity providers such as other Azure AD tenants, Facebook, Google, and enterprise identity providers. Admins can set up federation with identity providers so that your external users can sign in using their current social or corporate accounts rather than creating a new account specifically for your app.
B2B and B2C are the two types of Azure AD External Identities.
- B2B collaboration allows you to share your apps and resources with external users.
- B2C is an identity management solution for consumer and customer facing apps.
Concept of hybrid identities
Identity is generated in Windows Active Directory or another identity provider, then synced to Azure AD under the hybrid architecture. Identity creation and management are entirely handled by Azure AD under the cloud-only approach. Users can access both cloud and on-premises resources regardless of whether their identities are formed on-premises or in the cloud.
Users who access both on-premises and cloud apps are classified as hybrid users in the on-premises Active Directory. All changes to user accounts, groups, and contacts in your on-premises AD DS are synced to your Azure AD when you make an update. Azure AD Connect is used to handle the synchronization.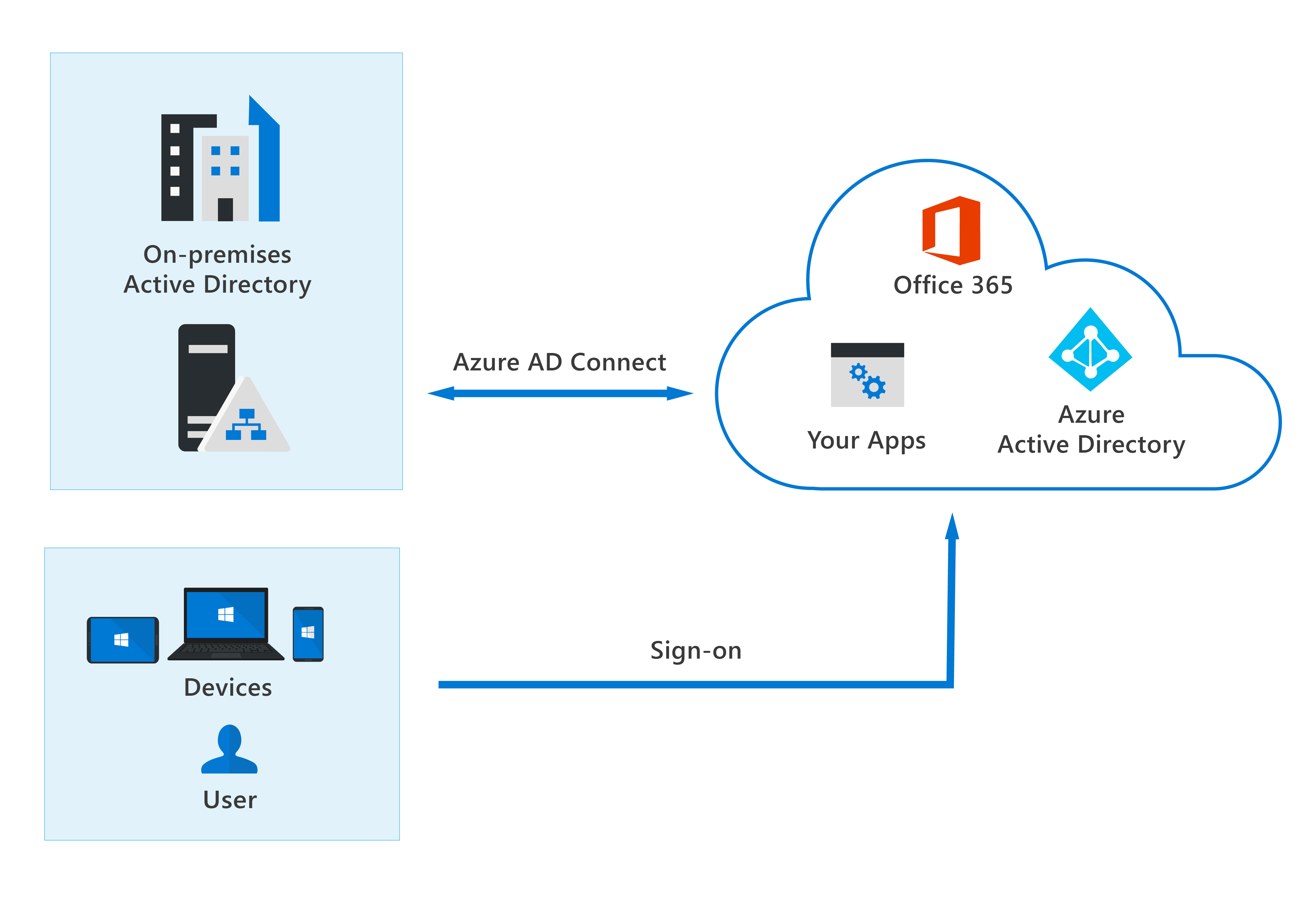
Authentication can be done by Azure AD (managed authentication) or by Azure AD redirecting the client seeking authentication to another identity provider (federated authentication) when utilizing the hybrid approach.










